What do we want? Data! When do we want it? Now!
With the rise in popularity and availability of smart devices, mobile computing has quickly become an exciting new frontier for developers of business applications. Companies on the cutting edge of technology are bringing the world closer to the visions of the science-fiction greats who imagined advancements like voice commands and cloud technology long before most of the world had even seen an actual computer in person.
Being able to say "Computer! Tea, Earl Grey, hot" and have a beverage spontaneously materialize in front of you may still be a futuristic dream (unless you've wired your kitchen appliances to your wi-fi network), but when it comes to data, restrictions no longer apply. With smart devices, any information that can be found on the Internet can be instantly delivered to our phones and tablets for on-the-go browsing. Not only have mobile devices changed when and how we view data, but they have also transformed what our society expects from data providers. Simply speaking, people no longer have any patience for information that cannot be obtained immediately.
Companies seeking to raise customer satisfaction have increased the availability of their data by expanding their web presence, but joining social media networks and creating mobile versions of websites are only good for the dissemination of public data. There are two types of information that a company needs to communicate with its customers: public data, such as product information, updates, and contact information—things that are the same for every customer—and private data, such as invoices, shipping orders, and contracts that need to be communicated on an individual basis. Figure 1 below breaks this dichotomy down visually.
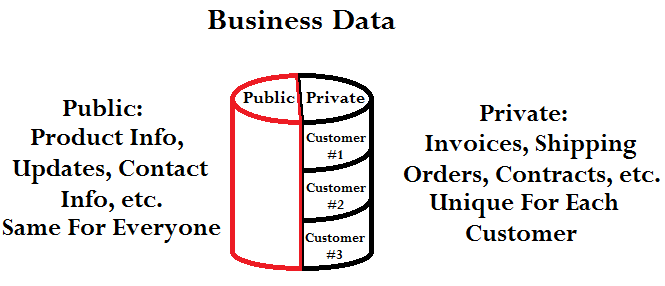
Figure 1: A company must distribute both public and private data to its customers.
Businesses face several challenges when attempting to make private data easily accessible to customers. It's difficult to create a system that's efficient and secure while still being affordable to implement. Many companies struggle to find an acceptable balance between the factors. While the optimal solution for efficiency and security is to have a website that allows users to register accounts and log in to view their private data whenever they want, it is also very costly to design and maintain the infrastructure of such web pages. Financial and medical institutions are forced to go this route despite the high costs because of the security concerns inherent with emailing.
Everything else being equal, if one company allows its customers to log into a website to see when their next service bill is due or to review their account history and reprint their latest invoice, and another does not, it is no mystery which one consumers will eventually gravitate toward.
Options for Success
As advances in mobile computing continue to raise customer expectations, what exactly can a company do to remain competitive?
Many have turned toward email for distributing private data. With the drop off of snail mail, email has risen to be the main source of communication for business data over the last decade and a half, but companies that distribute private data solely through email are forcing their customers to keep track of old attachments that often end up lost or deleted. This causes hassle for customers and employees alike when documents regularly have to be re-generated and re-sent. There's a conceptual flaw with using email as the primary source for private data as well: Email is sent on the company's schedule, not necessarily when the customer wants it.
Let's meander down a hypothetical road for a moment. You're a customer in need of a quote for a new product license. Company A does not have a website set up to do this automatically, so you have to contact them and give them information about who you are and what you want so that they can generate a quote and email it to you. All of this takes time, especially if you realize you need the information right after business hours have ended, possibly before a weekend or a holiday. Now you have to wait days before the quote shows up. You don't have time for that, so you turn toward Company B, who allows you to generate an instant quote through their website. Other scenarios may be less damaging to sales, but regardless of the type of information a company is providing, the faster a customer can get at it, the more satisfied they will be. Despite all of this, many businesses still do not want to bite the bullet and spend the capital required to hire programmers and designers to create and maintain a user-account-fed web page.
Anyone who doubts the importance of having instant access to private data need only ask themselves one question: In this day and age, would you sign up for a bank account that would only send you a bank statement once a month and wouldn't allow you to log in and view a list of all your most recent transactions? The vast majority of consumers certainly would not. People want fast, relevant, up-to-date data that is easy to access; our society is wired for it! Data providers must meet these high standards if they wish to maintain and build their customer base in this fast-paced age of technological advancement.
Should You Join the Cloud?
In the IBM i world, some shops are seeing the light and starting to turn toward cloud-based file-sharing services as a cheaper method for extending their mobile availability. This is quickly becoming a popular choice for smaller shops that either cannot afford a custom website or simply do not want to go through the hassle of maintaining one. Like email, cloud services have the same drawback in that a customer may want something like a quote, which must be requested before it can be provided to them, but on the plus side, storing data in the cloud keeps business files in one location, separate from the spam-filled melting pot of the customer's regular email inbox. Larger files, such as reports that are too big for conventional emailing, can be transferred through the cloud as well.
Logistically, however, shops that join the cloud are releasing control of their data over to off-site servers and letting the cloud service authenticate who is allowed to download files. This takes data security out of the originating company's hands, but it does not remove their liability should the cloud server's security ever happen to be breached. This is a frightening prospect, because without direct oversight of the data, there's nothing the originating company can do to mitigate any risk.
Even if security wasn't a concern, every person who wishes to access a shared document in the cloud must download a client program and register an account using their email address. While this may work for employees, the average consumer does not want to have to install special third-party software in order to view and manage their private data for some particular company. Cloud services are supposed to provide convenience, but putting extra steps between a customer and their data does just the opposite. Cloud services are typically more geared toward internal file-sharing within a company rather than sharing private data with customers. The difficulty of setting up these types of services on the user's end certainly adds to the problem.
On the distribution side, in order to securely share documents with customers, employees must place the documents in folders generated for each customer and then manually link the folders with registered users of the cloud service. Since customers register with the cloud service separately from the company, it can be difficult to verify that a folder is synced to the correct user. If a customer signs up to the cloud service with an email address that's different from the one on file within the company's records, the verification check will fail.
Become the Cloud
The IBM i has always been the midrange computer of choice for companies seeking to centralize and secure their business data while still maintaining high availability access for their users. Broadcasting out to a third-party cloud service removes the biggest advantage that the IBM Power Systems has over its competitors by removing data centralization.
Fortunately there is another option: Rather than building a custom website from scratch or handing over the reins to the cloud, there's software available on the IBM i that will allow a company to run its own cloud-like service and disseminate information directly from the IBM i. In this way, user registration and security can be handled internally, and there are no third-party systems that have to be relied upon or downloaded.
The IBM i has always acted like a cloud server; having centralized data is just like having a private cloud that allows employees to access business data from any computer connected to its network. By installing mobile application server software onto the IBM i, you can extend the network to include employees and customers connected via their mobile devices and off-site personal computers.
Generic mobile application servers provide a secure document delivery system at a low cost. A generic server will allow data to be distributed to customers through their web browser of choice using pre-fabricated web pages that only need to be turned on to start working. The generic server itself will provide all the built-in security, user sign up, and validation to keep private data secure. Distribution of both public and private data becomes a simple matter of placing files in folders on a host company's Integrated File System (IFS).
Packages already exist that can burst spooled files, convert the parts to PDFs with optional overlays, and place them in the appropriate IFS folders, making the entire process automatic and labor-free. Some servers can even provide full two-way communication, allowing users to make requests to the IBM i for what they want. With everything automated, a company can have tens of thousands of customers generating secure accounts and logging in through web browsers or mobile applications to view anything the company wishes to provide.
A Change in Thinking
Connecting the customer directly to the IBM i opens up many possibilities that have never existed before for midrange computing. If a customer needs a document, rather than having to wait for business hours to contact the company, the customer can log in to their account from any device or personal computer and request that the IBM i automatically generate the document for them right there on the spot. Depending on how the server is configured, the file can be immediately placed in the customer's folder, emailed, faxed, sent to a queue for processing, submitted on the customer's behalf, or simply displayed on their screen. The possibilities are wide open—true user-initiated, automatic communication at its best. Customers and employees alike can ask for what they want and have it delivered to them on their time table, not just when the company gets around to it.
Secure document delivery systems can work just like expensive custom websites, but they require less maintenance and are typically much more cost-effective. This type of software brings all of the power and security of the IBM i to the mobile world. Any business application or process in place on the IBM i can be integrated into the server software with relative ease, making things like presenting surveys to customers, generating and distributing documents, and submitting files for processing easier than ever.
Mobile application servers extend business processing to the mobile environment by giving companies a way to communicate complex information at the moment their users actually want it. By taking control of the cloud, your server can be more than just a drop box; it becomes a responsive entity for two-way communication with your users.
To sum things up, here's a breakdown of the pros and cons of each of the different systems discussed within this article:
|
Summary of Private Data Distribution Methods |
||||
|
|
|
Cloud Service |
Custom Website |
Mobile Application Server |
|
Instant 24-hour Access |
|
YES |
YES |
YES |
|
Secure |
|
??? |
YES |
YES |
|
Affordable |
YES |
YES |
|
YES |
|
No User-End Installation |
YES |
|
YES |
YES |
|
Large Files Possible |
|
YES |
YES |
YES |
|
Two-Way Communication |
|
|
YES |
YES |
"Computer! Clear my schedule. I'm going on vacation!"






















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online