Secure Sockets Layer (SSL) is a popular security scheme for encrypting data and requests between a PC and a server. You may want to take advantage of SSL when transferring sensitive data between a PC and a server—for example, transferring credit card or bank statement information. In this article, I’ll define the basic steps for getting SSL set up on an iSeries or AS/400 server and a PC using Client Access Express for Windows.
Overview of SSL
SSL is a public key cryptography technique that enables secure connections between server applications and their clients. Although SSL was originally developed for Web browsers, it can be used by any application that is written to use it. It has become an industry standard for securing communication between clients and servers. SSL is sometimes known as
“asymmetric encryption,” as the technology allows one party (that has a freely available public key) to communicate securely with another party (that has a private secret key). Although SSL is based on public key cryptography, its implementation actually uses both public and private key encryption along with digital certificates to authenticate the communicating parties. SSL’s strengths are providing privacy through data encryption, ensuring the integrity of message data, and authenticating the identity of parties exchanging data.
The flexibility, industry acceptance, and nonproprietary nature of SSL make it a perfect tool for doing secure e-business on iSeries and AS/400 servers. SSL uses digital certificates that contain public keys to prove identity between servers and clients. After a client determines that a server’s certificate is valid, the two systems negotiate a symmetrical key to use for the SSL session. These symmetrical keys expire automatically after 24 hours, and a different key is created for each subsequent connection. Consequently, even if unauthorized users intercept and decrypt a session key (which is unlikely), they cannot use it to eavesdrop on later sessions. This is accomplished through the use of digital certificates. (For information on the different types of certificates, see “Understanding digital certificates” on IBM’s iSeries 400 Information Center Web site at http://publib.boulder. ibm.com/pubs/html/as400/infocenter.html.)
Install SSL Applications on the Server
An increasing number of AS/400 and iSeries applications can use SSL to establish a secure connection between server applications and their clients. These are some applications and products that can use SSL:
• IBM HTTP Server for AS/400
• Telnet server
• Distributed Relational Database Architecture (DRDA) and Distributed Data Management (DDM) server
• IBM Management Central
• AS/400 Directory Services (Lightweight Directory Access Protocol, or LDAP)
• Client Access Express applications and applications written to the Client Access Express set of application programming interfaces (APIs)
• Programs developed with AS/400 Developer Kit for Java and client applications that use AS/400 Toolbox for Java
To use SSL, you must have the following programs installed on your AS/400 or iSeries server:
• Digital Certificate Manager (DCM), option 34 of OS/400 (5769-SS1)
• TCP/IP Connectivity Utilities for AS/400 (5769-TC1)
• IBM HTTP Server for AS/400 (5769-DG1)
• IBM Cryptographic Access Provider—either 5769-AC1 (40-bit), 5769-AC2 (56-bit), or 5769-AC3 (128-bit). The bit size for these products indicates the varying sizes of the digital keys they employ. A higher bit size results in a more secure connection. Note that some of these products are not available in all areas because of government export regulations.
Set Up the Server for SSL
To set up the Client Access Express servers to use SSL, follow these steps:
1. On the AS/400, use IBM Digital Certificate Manager (DCM) to manage digital certificates. Start the Digital Certificate Manager, and follow these steps to associate a certificate with the Client Access Express application IDs.
2. Click the System Certificates link.
3. Click the Work with secure applications link.
4. Click the button next to the application ID for the Client Access Express server that you want to secure. If you have not secured any servers yet, click the button next to the application ID for the sign-on server (QIBM_OS400_QZBS_SVR_SIGNON).
5. Click Work with system certificate.
6. Select the certificate from the list that you want the sign-on server to use to establish its identity to Client Access Express clients. (If you choose a certificate from a Certificate Authority (CA) whose CA certificate is not in your Client Access Express client’s key database, you will need to add it in order to use SSL. Adding CA certificates to the Client Access Express key database provides information on how to do this. Finish this procedure before beginning that one.)
7. Click Assign new certificate.
8. DCM displays a confirmation message. Click OK. The server will now automatically begin listening for incoming SSL connections, assuming you have started the Client Access Express servers before the DCM changes. To ensure that the servers are up and listening, you can issue the STRHOSTSVR *ALL command again.
Next, you need to enable one or more additional Client Access Express servers, depending on what applications you plan to run. Figure 1 shows the application IDs for these servers.
To enable Operations Navigator, you need to assign a certificate to all of the QZBS servers. If you want to use the Management Central functions, you need a certificate for the Management Central server. PC5250 emulation and Data Transfer need certificates assigned for the Telnet, Central, and Sign-on servers. ODBC needs certificates assigned for the Database and Sign-on servers. There is no harm in using the same certificate for all applications, just as there is no harm in assigning a certificate to applications that you do not intend to enable to use SSL. See Information APAR II12227 on the Client Access web page at www.iseries.ibm.com/clientaccess for more information on which servers to enable.
Set Up the Client for SSL
There are several steps required to enable SSL on Client Access Express clients. Because of export regulations for products that contain encryption technology, the client encryption products are installed with the data authority set to *PUBLIC EXCLUDE. The products are located at QIBM/ProdData/CA400/Express/ SSL/SSLnum, where num is the bit key length (40, 56, or 128) for the version of the client encryption product you are using. You must then authorize the appropriate user IDs to the client encryption products.
If you do not have Client Access Express installed, you can do so from an AS/400 command prompt. If you do have it installed, you can use Operations Navigator to grant users access to the encryption products. First, start Operations Navigator. Next, expand your AS/400 system, expand File Systems, expand Integrated File System, expand Root, expand ProdData, expand CA400, expand Express, and expand SSL. Then, right-click on SSLnum—where num is the bit key length (40, 56, or 128)—for the version of the client encryption product you are using, and select Permissions. Use the Permissions dialog box to give Public Read and Execute authorities or to add specific users and groups to the object’s authorization list.
Now you need to install the AS/400 client encryption products—5769-CE1 (40- bit), 5769-CE2 (56-bit), or 5769-CE3 (128-bit)—on the PCs. As with the Cryptographic Access Provider products, the bit size for these products indicates the varying sizes of the digital keys that they employ. (Some of these products may not be available in all areas because of government export regulations.)
To install Client Access Express, follow the instructions in topic 3.3.1, “Using AS/400 NetServer to install Client Access Express,” of the book Client Access Express for Windows—Setup V4R5M0. When the Install Wizard displays the Component Selection window, be sure to select Secure Sockets Layer (SSL) and the appropriate client encryption product under it.
If you already have Client Access Express installed, use Selective Setup to add the SSL component. To start Selective setup from the Windows desktop, click Start/Programs/IBM AS400 Client Access Express/Selective Setup. (Note that you must use AS/400 NetServer to install the SSL component directly from the AS/400 system, even if you previously installed Client Access Express through another method. This is because of regulations that govern the distribution of programs that use encryption technology.)
Add Certificate Authority Information to the PC Key Database
Adding Certificate Authority information (i.e., who signed and created certificates) to the Client Access Express key database allows the AS/400 server to establish an SSL connection to the client using a certificate from that Certificate Authority. If your Client Access Express servers use certificates from certain well-known certificate authorities, you can skip this step, as some well-known Client Access certificates come preloaded in the key database. If you are using the AS/400 to create digital certificates, there are two steps to adding a Client Access certificate to the key database.
First, you must copy the certificate from the AS/400 system to the PC. Client Access provides the cwbcossz.exe utility to help you with this process; it is available on the Client Access Express home page (www.as400.ibm. com/clientaccess/cwbcossz.htm). If you do not want to use that utility, follow these steps to download the certificate:
1. Start Digital Certificate Manager.
2. In the left frame, click Certificate Authority (CA).
3. Click Install CA certificate on your PC.
4. In the right frame, click Copy and paste certificate.
5. Select the text from BEGIN CERTIFICATE to END CERTIFICATE.
6. From your browser’s Edit menu, select Copy.
7. Start the Notepad application on your PC. From the Start menu, select Programs, Accessories, then Notepad.
8. From Notepad’s Edit menu, select Paste to insert the certificate text into the document.
9. From the File menu, select Save. It is suggested that you use the file name CA-.ARM and save the file to the main Client Access Express installation directory (by default C:Program FilesIBMClient Access). However, you may choose any file name and location. Use the file extension .arm rather than the default .txt.
Now you need to add the certificate to the key database. Follow these steps to add the certificate:
To start the IBM Key Management application, click Start/Programs/IBM AS400 Client Access Express/IBM Key Management. From the Key Database File menu, select Open. The default file name for the key database is cwbssldf.kdb. It is located in the root directory for Client Access, so by default it would be located at C:Program FilesIBMClient Accesscwbssldf.kdb. Browse to this file, select it, and click Open.
You will be prompted for your password. Unless you have previously changed the password from the default, enter ca400. Click Add. Click Browse, then browse to the file that you have created, select it, and click Open. Click OK.
When prompted, enter a label for the certificate. It is suggested that you use the Client Access Express AS/400 system name for the label. Click OK.
Note that certain functions of Operations Navigator use Java, so you need to additionally download the Certificate Authority information into the Java database manually or use the cwbcossz utility (described earlier) to set it up.
Client Access Express can now use the CA certificate.
Set Up Client Access Express Use of SSL on Your PC
Now that you have installed all the appropriate software for use with SSL, you must configure which portions of Client Access you want to use it. Client Access Express applications that can communicate over an SSL connection include Operations Navigator, PC5250 emulation, Data Transfer, and ODBC.
You can also use the Client Access Express APIs to create applications for Client Access Express that can use SSL for secure communications. The only Client Access Express functions that cannot be used with SSL are Ultimedia Systems Facility (USF), messaging application program interface (MAPI), and Incoming Remote Command (IRC).
When you install Client Access Express, a small part of Operations Navigator is automatically installed so that you can work with your various AS/400 connections through the AS/400 Properties page shown in Figure 2. To find the AS/400 Properties page, start the AS/400 Operations Navigator, right-click on the desired AS/400 system, click the Properties tab, and then click on the Connection tab. The Use Secure Sockets Layer (SSL) box can be used to turn SSL on and off.
You can enable or disable SSL for Operations Navigator through the Properties page. By default, if you enable SSL for Operations Navigator, it will then be enabled for all other Client Access applications that are started from that point on (including third-party applications that use Client Access APIs). To ensure that all functions are SSL-enabled, you should close and restart the connection. You will then see a padlock on the AS/400 name that indicates that SSL is enabled for this connection.
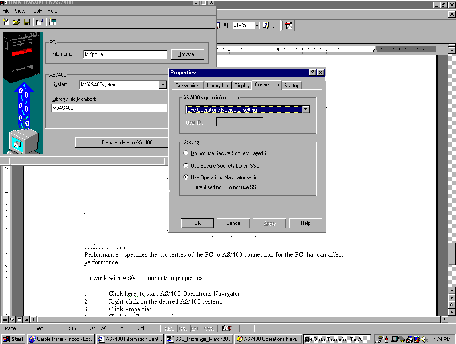
Default values set through Operations Navigator can be overridden at the application level. You can enable or disable SSL separately for the following functions as you use them: PC5250 emulation, Data Transfer, and ODBC. See Figure 3 for an example of the actions you can specify through Data Transfer—i.e., Do not use Secure Sockets Layer (SSL), Use Secure Sockets Layer (SSL), or Use Operations Navigator setting.
You can use the Client Access Policy support to set up your PC users so that they must use SSL when connecting to an iSeries or AS/400 server. If a policy has been set mandating the use of SSL, any connection attempt that cannot use SSL will fail. This means that, if the user does not have SSL installed, or if the AS/400 system is incapable of using SSL or does not have the SSL-capable versions of the host servers started, no connection to that server can be made. It is not possible to mandate that SSL be turned off, as users can elect to use SSL, assuming that it is installed and configured on both the AS/400 server and the client PC. For information on how to set up a policy for SSL, go to the Client Access Web page (www.iseries.ibm.com/clientaccess) and select Information Center - Express Client (XE1) from the left-hand panel, which takes you to the iSeries 400 Information Center. Select Client Access Express (on the left-hand panel). Then select Policy administration (under the subheading Administering).
It’s Easy, Once You Know How
As you can see, there are several steps you must go through to set up SSL on the server and clients in your network. Fortunately, the complexity inherent in SSL isn’t reflected in its practical application. Once the SSL tasks have been completed, it’s relatively easy for users to use this secure environment to communicate with servers using SSL.
Beyond SSL
This article addresses capabilities available through OS/400 V4R5 and when using Client Access Express for Windows. Watch for a future article on improved SSL capabilities being provided in the next releases of OS/400 and Client Access Express.
Another method for securing communications is through Virtual Private Networks (VPNs). Client Access Express users running Windows 2000 can directly connect to OS/400 V4R5 and use VPN, which encrypts the entire session conversation. For more information on this alternative, see Information APAR II11791, “Client Access Express Support Position on VPN Connectivity” on the Client Access Web page at www.iseries. ibm.com/clientaccess.
REFERENCES AND RELATED MATERIALS
• AS/400 Certificate Authority Downloader Utility (cwbcossz.exe): www.as400.ibm.com/clientaccess/cwbcossz.htm
• Client Access Express for Windows—Setup V4R5M0 (SC41-5507-01, CD-ROM QB3ACN01)
• Client Access Web page: www.iseries.ibm.com/clientaccess
Server Name Application ID
Central server QIBM_OS400_QZBS_SVR_CENTRAL Database server QIBM_OS400_QZBS_SVR_DATABASE Data queue server QIBM_OS400_QZBS_SVR_DTAQ File server QIBM_OS400_QZBS_SVR_FILE Net print server QIBM_OS400_QZBS_SVR_NETPRT Remote command server QIBM_OS400_QZBS_SVR_RMTCMD Signon server QIBM_OS400_QZBS_SVR_SIGNON Management Central QIBM_OS400_QYPS_MGTCTRL_SVR Telnet QIBM_QTV_TELNET_SERVER.
Figure 1: These are the names (application IDs) for Client Access Express servers.
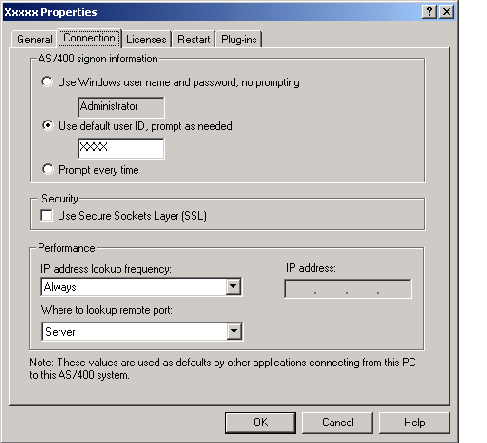
Figure 2: Use the Client Access Express Properties page to configure SSL.
Figure 3: Here are some of the SSL options and actions you can specify when using Data Transfer.



















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online