In this 2009 update of one of MC Press Online's most popular ever articles, learn how you too can have amazing superpowers.
When I was young, I used to fantasize about having superpowers. Even after I had learned the laws of physics, I still yearned for the abilities to fly, to become invisible, and to travel through time. After becoming a systems management professional, I had to accept reality and put away my dreams of wielding superpowers.
However, let me tell you about a piece of software called System i Navigator. This application is nothing short of amazing and, as you will see, is the source of many superpowers. If you always wanted to become a superhero*, then read on. You may not be able to save the world, but at least you'll be able to save your IT shop!

Figure 1: Be an IBM i superhero!
*Disclaimer: <read in a highly legal-sounding voice> Although System i Navigator has a wide variety of function, it will not enable you to fly, become invisible, or travel through time.
Your Superhero Utility Belt
Any superhero worth anything has a utility belt. Superman? A wimp. He just kind of fell into it because of the color of our sun. Real superheroes like Batman, James Bond, and Tim Taylor have awesome utility belts. These are ordinary people overcoming incredible odds with really cool technology. You and I are also ordinary people who can overcome the odds of managing our IBM i systems by using really cool technology.
So what do you need on your utility belt to become a superhero in your IT shop? System i Navigator is one. Systems Director Navigator for i is another. Over the years, System i Navigator has evolved into a robust Windows-installed application filled with rich functions to manage your IBM i systems. It uses visual technologies to help you beat the IT villains and provides an easy-to-use interface ready to help in your glorious battles. More recently, Systems Director Navigator for i is the Web-based console on every IBM i operating system that provides many of the System i Navigator tasks from a Web browser.
So what, exactly, can System i Navigator do to enable you to become a superhero? Plenty. In fact, several superheroes are already fighting the good fight using System i Navigator. Maybe you'd like to become one of these superheroes? Maybe you want to become a customized superhero? Here are some of the current superheroes out there today that you could become based on your background, education, and talent.
Lizard Man: He Can Make Anything Intelligent

Figure 2: Lizard Man controls intelligence!
The first superhero you could become is Lizard Man. Lizard Man's main superpower is that he can make anything intelligent.
How can he do this? Let's take a look.
Using the various monitors in System i Navigator, Lizard Man can make intelligent decisions and make his IBM i system begin to manage itself. Each monitor type (system, job, message, and file) has a number of metrics. Each metric has information that can be customized so that Lizard Man can choose what behavior he is interested in paying attention to. In addition, when triggered, each monitor can run a command. This is where the intelligence comes into play: the command can be a program, written by you, and can be passed several replacement parameters from the monitor. These replacement parameters dig down to the details of why the monitor triggered. For example, when a job monitor triggers, a program can be called to change a job's priority or to move a set of jobs to another job queue. It can do this because the replacement parameters can pass the job name, the trigger value (how much CPU it's using or what status it's at, etc.), or any of a number of other values. Figure 3 shows the part of the monitor properties where you can specify to run a program.
Figure 3: Specify an automation program in the monitor properties view.
Once these monitors and associated programs are set up, a number of intelligent actions can be done. Here are just a few examples to get your mind thinking:
- If the system is at 80 percent CPU, change priorities of offending jobs
- Find jobs waiting for locked objects and process those objects
- Automatically reply to inquiry messages based on current environment
- Notify a human if HTTP servers are too busy, hung, etc.
- Find out if an important file has been changed
The Profile Wrangler: He Can Create Life and Control Destiny

Figure 4: The Profile Wrangler controls the destiny of others!
Maybe the Profile Wrangler is a better fit for you. The Profile Wrangler's main superpower is that he can create life and control the destiny of others. Pretty powerful! How can he do this? You guessed it, by using System i Navigator (or the Web-based Navigator for i).
Using the Users and Groups support in System i Navigator, the Profile Wrangler can create users across multiple systems based on a definition, he can edit multiple users across multiple systems, and he can search for users across systems. The best way to show this superpower is by using a few examples:
- The Profile Wrangler needs to create a test user for Batman. Since all test users generally have the same authorities and access needs, the Profile Wrangler selects a user definition called Testers. He selects Create User from the definition and then enters the ID and password. The profile is created across systems, just like that! But that's just the start. In each definition, there's an Action page that lets the Profile Wrangler specify a program to run once the profile is created. So now, instead of having to sign on to those 30 systems that the new profile was created on, the program has automatically been called to add a library, add the profile to authorization lists, assign authority to special objects, and create home directories and files in IFS. Wow, that is super!
- The Profile Wrangler needs to edit eight users across 15 systems because a person has changed departments. This person has eight profiles on each system (one for testing, one for developing, etc.). Using the Edit Users function in System i Navigator, those eight profiles can be selected, and the Department field can be selected from Personal Information, and again, just like that, the profiles are updated across all 15 systems. If you tried to do that the old way, you'd have to enter 120 commands!
- The Profile Wrangler needs to find all users who are using more than 8 MB of storage. By selecting the system group of the 10 systems to search on, he selects Inventory->Search. Then, he can choose from a number of advanced items to search for users and groups. In this case, he selects Storage Used and > 8 MB. The search results come up showing all users across those 10 systems who are using more than 8 MB of storage. He can then act on those users (edit, disable, etc.) or export the entire list so he can send it to their manager to inquire about the storage.
The Wireless Wonder: She Has ESP

Figure 5: The Wireless Wonder knows all!
The Wireless Wonder is a great superhero to become for those of you who really like cool tools on your utility belt. There's no end to the fancy devices you can have dangling from your hip if you're the Wireless Wonder. Her superpower is that she uses ESP to know all. By using System i Navigator for Wireless, she can use Exciting devices to connect from anywhere, see Summary views of all she cares about, and take Powerful actions on objects.
The secret power behind System i Navigator for Wireless is that it's a true companion to System i Navigator. By using System i Navigator on your central system to set up monitors, run tasks, add endpoint systems, and create system groups, you can manage all those items from System i Navigator for Wireless.
Let's look at the secret powers of what the Wireless Wonder can do from anywhere, at any time.
The first secret power the Wireless Wonder can use is that she can view an overall summary of all she cares about from one view on her Internet phone. The status of all the monitors, tasks, and systems is summarized down to one word--either OK or Attention--as shown in Figure 6. If anything she cares about needs attention, the overall status will show as Attention, and the summary page will point to where the problem is.
Figure 6: View the status of all the monitors, tasks, and systems via a cell phone.
The second secret power she can use is the ability to take powerful actions from anywhere. Here are just a few examples of what can be done from a wireless device:
- Run a command across a System i system group (by using a definition or by entering a command)
- Run a command across multiple xSeries servers
- Restart or shut down one or multiple xSeries servers
- Hold or delete a runaway job
- Answer an inquiry message (from QSYSOPR, any message queue, or a job's job log)
- Start, stop, or restart monitors
- View status of long-running tasks
- View properties of objects
One recent addition is that the Wireless Wonder can access any wireless network with her laptop and then use the Web-based Navigator for i to run over 300 tasks. In V5R4, many of the tasks were added; then in V6R1, the full Navigator for i Web console became available. Using Navigator for i, she can get to all the core systems management tasks from her browser, including these:
- •Printer Output
- •Jobs
- •Messages
- •Work Management
- Values
- •Database
Navigator for i provides additional benefits as well:
- •You can access multiple systems through one system that the Web browser interacts with.
- •It uses a Java servlet and portlet application (your choice). If you go to the :2001 port in V6R1, you will see Navigator for i using portlets to show the Web-based tasks. However, you can also go to the Navigator URL Advisor (under the Internet category in Navigator for i, or right on the :2001 port in V5R4) to view servlet versions of the Web-based Navigator tasks. The value of the servlet versions is that those can be embedded into other Web apps since they are all directly URL-accessible.
- •It runs the same binaries as System i Navigator (meaning the same look and feel)
- •System i Navigator Web tasks can be embedded into other Web applications
Pretty-Boy Malloy: He Can Make Anything Beautiful

Figure 8: Pretty-Boy Malloy is stunning!
Now, to be honest, in order for some of you to qualify to be Pretty-Boy Malloy, you'll just have to become much more attractive (just kidding). This is a very popular superhero, because System i Navigator has many fancy, colorful ways to display and interact with data. Here's a small list of some things Pretty-Boy Malloy can do:
- Stun them with graphical performance history: Use the graphical monitors and graph history to show real-time data, as well as historical data over a day, week, month, year, or more. These graphs can be manipulated to find problem areas or bottlenecks and can be captured for later viewing. Starting in V5R4, you can even save, print, coordinate, organize, and customize these graphs for better reporting.
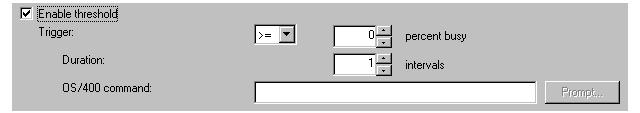
- Stun them by interacting with pictures of your System i: Use the Disk Units Graphical View to view pictures of multiple System i towers; see where the disk units are physically located; and work with the disk units, disk pools, mirrored pairs, and all the other groupings disk units can have (as shown in Figure 8). Once this view is opened, Pretty-Boy Malloy can even mouse over an empty slot and open a wizard to add a disk unit. Starting in V5R4, he can print the Graphical View for records and reference.
Figure 8: The Disk Units Graphical View shows all the groupings disk units can have.
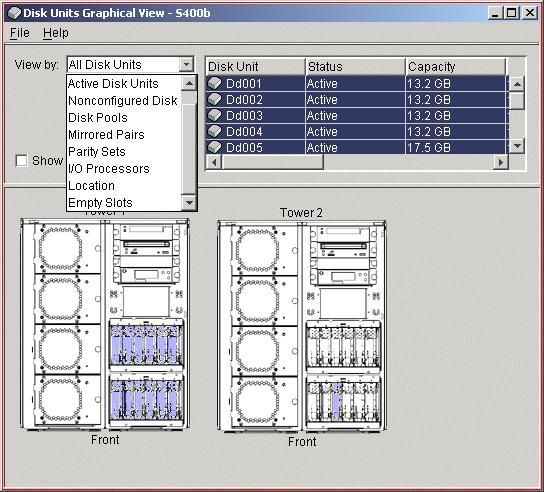
- Stun them with Web-based graphical views of historical data: Using the Web-based Navigator for i in V6R1, Pretty-Boy Malloy can see many different views of historical performance data from a browser (Figure 9). This provides a rich set of graphs, as well as custom views that can be printed and saved.
Figure 9: Navigator for i shows performance history.
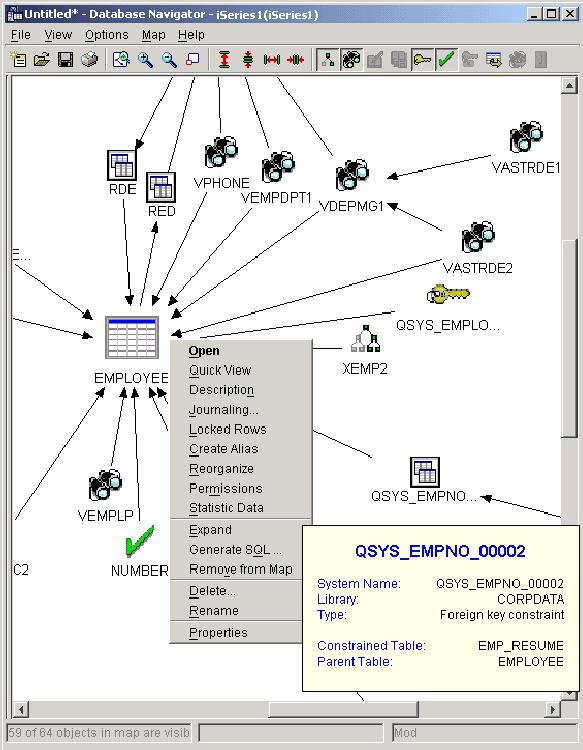
- Stun them with visual layouts of the database: Using Visual Explain in System i Navigator, he can view the layout of his database, see how the tables are generated, and even select objects and work on them immediately. The layout shows bottlenecks and points where improvements can be made, as shown in the example in Figure 10.
Figure 10: Database Navigator shows relationships and tasks for your database.
The File Master: He Can Be Omnipresent and Can Wield Telekinetic Morphing Powers

Figure 10: The File Master is everywhere all the time!
This particular superhero is already quite popular in Hong Kong and has his own movie coming out next summer, so if you want to become this superhero, act soon so you can get in on all the royalty rights. The File Master has two superpowers: he can be omnipresent, and he can wield telekinetic morphing powers on demand. He can accomplish this by using the file monitor and the "send files and folders" function in System i Navigator.
Using the file monitor, he can point to any file on one or multiple IBM i systems and find out whether it changes, gets bigger than a certain size, or contains a particular text string. For example, if there is an important file, he can know at any time if it's been modified. Or, if he has a log file, once it reaches 5 MB, he can have it automatically archived and cleared. The list goes on and on.
Starting in V5R4, the File Master can display the contents of the System i history log, accessible from Configuration and Service. By default, the history log shows only the messages from the previous hour, but by using Include, he can customize what is shown by date and time, job, or message ID. Finally, from a context menu, the File Master can work with the job that issued the message.
By creating a package definition, the File Master unleashes the power of telekinesis. A package definition can point to any combination of files in IFS or any combination of files in QSYS. Then, the file master can tell the definition that, when it is sent, it must change the directory in which a file is located on the target system or change the name of the file or folder once it arrives on the target system. This is great for sending a program located in MyTestLib and locating it in MyProdLib on the production system.
The Compare and Update Kid: He Can Clone Anything
Figure 12: The Compare and Update Kid makes clones!
This spunky little fellow's superpower is that he can clone anything he touches. Using System i Navigator, he can compare and update fixes across systems, as well as compare and update system values across systems. The idea behind these compare and update tools is that once a single system is working great (meaning it behaves in a desired way), he can select to compare that "model" system to any number of "target" systems to see what's wrong on those target systems. The compare and update fixes will show what fixes are missing and what fixes are extra on those target systems--with the ability to have System i Navigator send, install, and even restart the IBM i systems once all the fixes are installed.
The compare and update system values give him a workspace where he can select any system value and see its corresponding value on the target system, and if it's not what he wants, he can select to update that value.
Each of these updates can be scheduled so the updating can be done in off hours or when traffic is at its lowest.
A bonus super tool that the Compare and Update Kid uses is the Synchronize Date and Time function. This handy little function lets him select a model system and synchronize the time across multiple target systems based on that model system's date and time. When doing anything with multiple systems (viewing real-time graphs, for example), hundreds of headaches will be saved per day by having times synchronized. This function can also be scheduled, so a common example would be to schedule to synchronize the date and time every Sunday at 2:00 a.m. so it's all set for the week.
The Dynamic Attention-Deficit Duo: They Can Move Quickly from One Task to Another

Figure 13: The Dynamic Attention-Deficit Duo move quickly between tasks.
With all the TV and video games wreaking havoc on our attention span, these superheroes could be just for you. Armed with quick-hitting, short-running power tools, the Dynamic Attention-Deficit Duo uses System i Navigator to get the job done without having to focus too much on one thing.
One common problem for the Dynamic A.D.D. is that they can't focus on one task too long, but each task requires a different profile. System i Navigator usually only lets a user sign on with one profile. Well, by using the following trick, a single system can be signed onto using multiple profiles in the same System i Navigator window. Here are the steps:
- Add System1 as a connection to System i Navigator.
- Search on your PC for your "HOSTS" file.
- Edit the hosts file and add an alias to System1 called System1a.
System1a 3.4.5.6 (the IP address of System1) - Add System1a as a connection to System i Navigator.
- Sign on as two different users.
System i Navigator also includes drag-and-drop functionality, and since V5R2, the Dynamic A.D.D. can use it to interact with a large number of objects. For example, they can change the priority of a job in a job queue by simply dragging it up or down the list. Or select a file or folder and drop it to a system group. Or select eight fixes and drop them on a system to send or send and install them. One particular example stands out: drag printer output to the desktop, and it will appear as a text file on the desktop, which is great for emailing or adding to a report.
Lists of objects are very common for System i Navigator. Some are small, but some are large and fairly unfriendly because of the hundreds (or thousands) of items in the list. By using the Sort, Include, and Columns support, the Dynamic A.D.D. can decide what's important and see only that in the list. Sort will sort the items in the list based on information in the selected columns. Include lets the Dynamic A.D.D. choose those characteristics they are interested in and then shows only those items that match. Columns lets them choose which columns to show and hide and in what order. Using these three tools makes all the specified items appear right away at the top, so there's more time spent solving problems than trying to find problems.
You Can Be a Superhero!
As you can see, there are a number of superheroes you can become to save your IT shop. Strapping System i Navigator and the Web-based Navigator for i onto your superhero utility belt will enable you to triumph over the most menacing foe. And just like Batman has Alfred as his backup support, System i Navigator has the System i Navigator Web site as well as the System i Information Center. Go to the System i Navigator Web site to learn more about what System i Navigator can do and to view demos, FAQs, and all of the presentations we do at various user groups. Go to the System i Information Center to gain a deeper understanding of how to best use System i Navigator, as well as all its related function.
I hope you had a fun time learning what System i Navigator can do. And as they say, "Stay tuned--same iTime, same iPlace--to see what villains you can defeat!" Next time, I'll introduce a whole new set of superheroes you can become by using the recently released IBM Systems Director 6.1!





















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online