Editor's Note: This article was revised and updated from an article previously published in MC Mag Online.
At the advent of the new millennium, the world's largest retailers heralded Radio Frequency Identification (RFID) technology as the key to the supply chain of the future, with the potential to save billions of dollars in inventory-handling and tracking costs. Within a few years, several of the larger retailers, Wal-Mart and Target in particular, as well as the Department of Defense (DoD) set deadlines by which their largest suppliers were to ship pallets and cases with RFID tags identifying the contents. Although many of the deadlines have come and gone without achieving broad compliance—primarily because standards and technologies are still being sorted out and costs haven't dropped as quickly as expected—this hasn't lulled manufacturers and distributors into complacency about RFID. Most know that the broad use of RFID in the supply chain is inevitable.
Today, what's surprising is that the adoption of RFID within supply chain companies is happening on its own—without being pushed by mandates from the major retailers. This is a very different situation from three years ago when suppliers were typically adopting RFID only because of mandates. This change is a clear sign that most companies are seeing the benefits of RFID for themselves.
There are still kinks to be worked out regarding environmental factors, security, and an often-challenging implementation process, and the issue of standards is still to be settled upon. But despite this, RFID has already reached astonishing levels of versatility, economy, and pervasiveness. Considering the steady dropping of costs associated with purchasing and implementing RFID technologies, it is likely that the vision of RFID being used across the supply chain may actually be realized.
Not only does the technology eliminate the line-of-sight and serial scanning limitations of barcodes (i.e., a pallet of merchandise can be instantly inventoried without taking the pallet apart and scanning each case), there are many greater savings and efficiencies once the technology finally gets perfected and proliferated. For example, RFID can provide instant inventories of entire warehouses, automatic triggering of restocks/reorders when products leave store shelves, instant tracking of recalled products, and much more.
RFID Anatomy
RFID usage is not much more complex than barcode usage. With barcodes, each tag contains an identifying code, which when read by the appropriate device, links the item to other information in back-end databases. But instead of reading lines or dots on a label and translating it to a part number, RFID uses an integrated circuit (IC) chip about the size of a pinhead that can be programmed with a part number (and a whole lot more) and attached to a mini antenna. This device is activated by an electromagnetic field, which in turn initiates a process of transmitting the chip's data to a nearby receiving antenna and relaying it to a back-end computer. As you can imagine, the applications beyond supply chain usage are endless—from medicine to security to logistics to transportation to just about anything you can think of. Of course, it's also easy to imagine more nefarious uses, like stealing identities and invading privacy, which are very real concerns. Still, the benefits are remarkable in terms of positive identification, efficiency of processes, improvement of quality, and reduction of theft and forgery.
The RFID Tag
As mentioned, the RFID tag (also called a "transponder") is made up of an IC memory chip and an antenna and, in some cases, a battery to boost the signal. RFID tags are available in a spectrum of shapes and sizes: They can be thick and rigid or thin and flexible enough to be embedded within an adhesive label and run through a label printer to provide visual identifying information. These long, paper-thin, disposable tags are often used to identify pallet loads and caseloads of merchandise to entities in a supply chain. The type of tag simply depends upon what it needs to deliver in terms of quantity of information, range of transmission, durability, and the operating environment.
Figures 1 and 2 show a simple RFID tag. As you can see, there isn't much to it in its basic form. Most of the size of the tag is taken up by the antenna, the size of which is dictated by the needed detection range.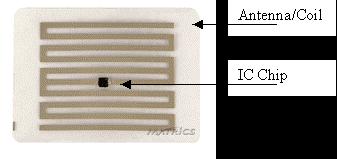
Figure 1: A simple RFID tag (courtesy Matrics)
Figure 2: Square chip/antenna inlay for rigid carton tags (courtesy Matrics)
Typically, the larger the tag, the larger the memory capacity, the greater the durability, and the more extended the range in which the tag can be detected. In addition, different tags transmit at different frequencies, depending on the application and the reception/transmission range needed.
Tags can be read-only (programmed once only), read/write-capable (reprogrammed multiple times), or a hybrid of the two (certain data can be permanently written—for instance, a serial number—while other data can be changed or added as needed—for instance, purchase and warranty information). Read-only tags are preprogrammed or encoded when they are manufactured (i.e., when large quantities of tags have the same information) or are programmed just prior to the tag being attaching to an item, sometimes by the same device that detects and reads the tags (the reader).
RFID tags are either "passive" or "active." Passive tags are activated by the energy field that is transmitted by the reader. Because passive tags do not have their own power supply for transmitting encoded information to the reader, their detection distance from a reader is greatly limited. Active tags are each powered by their own battery, which adds cost but significantly extends the detection range. Of course, active tags are usually more expensive and heavier than passive tags. Active tags can cost several dollars each, while passive tags can be purchased for as little as 10 cents each (in large quantities). Because of the price, passive tags are typically the tag of choice in the supply chain and then mostly at the case and pallet level; however, within the next few years, it is expected that the price of passive tags will drop to a few cents each, at which point RFID will begin to replace barcodes on individual products.
To comply with the mandates of large retailers, a special RFID tag called a "smart label" is often used. A smart label (Figure 3) is essentially a barcode label that has a flat RFID tag embedded inside. 
Figure 3: Flexible, adhesive-backed "smart label" (courtesy T.L. Ashford)
The RFID tag within smart labels is typically coded with an Electronic Product Code (EPC) and any additional information required by the customer (more about EPCs shortly). The cost for smart labels has dropped to less than 10 cents each in quantity, while the printers that accommodate both the printing and programming of smart labels go for between $1,000 and $5,000, depending on needed functions. In addition, it is necessary to ensure that back-end software can accommodate the RFID data passed to the printer/encoder. For some companies, this latter requirement can be expensive, especially if the software needs to be changed to accommodate RFID data.
RFID Readers/Interrogators
Besides the tag, the most critical component of RFID technology is the "reader" or "interrogator," which gleans the information from the tags. Readers transmit an energy field that causes a tag to activate and then transmit the data stored within its chip to the receiver on the reader. If the tag doesn't have a battery, the reader's energy field provides the necessary power for the tag to transmit its information back to the reader, although the detection/transmission distance is significantly reduced. When data is received by the reader, it's passed along to back-end computing systems in order to initiate actions and transactions.
Like barcode scanners, readers can be fixed or portable. Fixed readers range in size from floor models that are as tall as a person to smaller handheld units the size of handheld barcode readers. It simply depends on the application. These units typically collect data on products traveling through "choke points" such as dock doors, conveyor belts, etc. Portable, wireless readers can be attached to forklifts and collection carts.
Not only do readers locate, activate, and receive transmissions from RFID tags, many have the capability of sending data back to read/write-capable tags to either add or replace information. In addition, RFID technology allows hundreds of tags to be read simultaneously, and individual tags can be read as fast as 100 milliseconds per tag.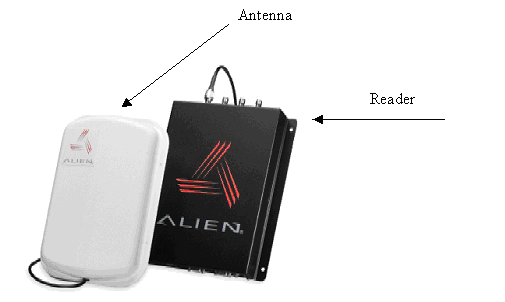
Figure 4: RFID reader and antenna (courtesy Alien Technologies)
Figure 5: Handheld reader/interrogator (courtesy Intermec)
EPC Codes and Standards
The EPC (a.k.a. Global Trade Item Number, or GTIN) is the basis of an enhanced global supply chain network that RFID is propelling. The EPC is substituted at the pallet and case level for the well-known Universal Product Code (UPC). EPC codes are necessary when RFID is used in supply chain applications for two reasons: First is to create globally accepted standards for product identification. Products around the world must be identified and described in a standardized way, and communications about product attributes between partners must also be standardized (UPC codes are limited to use only in certain geographies). Second, EPC provides the potential to uniquely identify every item that is produced. For instance, each gallon of milk can potentially have a unique ID number that indicates the manufacture date, the plant where it was bottled, the lot number, the expiration date, etc.
Today, serial numbering is not yet cost-effective unless the item has a high value, but once tags get down to a few cents each, serial-numbered RFID tags will likely appear on many kinds of items. This will provide a variety of benefits to retailers; for instance, as previously mentioned, a retailer will be able to automatically detect when shelves need to be restocked (which can in turn trigger the automatic generation of purchase orders).
EPC codes are obtained from an organization called EPCglobal, are typically made up of 96 bits of information (24 four-bit characters) and are programmed onto RFID tags to identify the manufacturer and type of product (as barcodes do today). In many instances, companies use their present UPC code within their new EPC code. Until the cost of RFID tags reach cents-per-piece levels, many companies will use RFID codes only to track items at the SKU level (identifies manufacturer and product type) and then only in case and pallet units of measure. Even so, this currently complies with the mandates of Wal-Mart and the like. 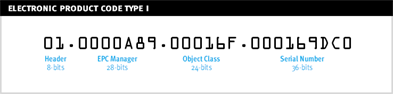
Figure 6: A 96-bit EPC code (courtesy LANSA)
In Figure 6, the portion of the code shown as the "EPC Manager" identifies the company, while the portion of the code shown as the "Object Class" identifies the brand, model, size, unit of measure, etc. Finally, the last portion, the "Serial Number," can be used to optionally identify the individual product.
Before a company can program EPC codes into RFID tags to meet basic RFID compliance requirements with major retail customers, they must ensure their EPC codes meet global standards, and the EPC codes must be must be registered within the Global Data Synchronization Network (GDSN). Essentially, GDSN is a private "Internet" for global trading partners that allows partners to access standardized information about a product.
The Potential of EPC
The purpose of EPC codes is to create globally accepted standards for product identification. Products registered on GDSN can have up to 200 standardized product attributes that can be seen and shared by all current and potential trading partners. For instance, when a vendor introduces a new product and its EPC code is registered on the network, a "catalog item notification" can be automatically distributed to all retailers connected to the GDSN. These retailers can instantly access complete standardized product information and decide whether to stock the item. If a retailer decides to purchase the item, an instant notification can be sent to the vendor. In addition, if a vendor makes any change to the product attributes, a "catalog notification" can be automatically distributed to all retailers, advising of the change. This system can also be very valuable for recalls because vendors can immediately know all of the purchasers in the supply chain.
EPCglobal Frequency Specifications for RFID
EPCglobal has created different specifications for the frequency, encoding characteristics, and other attributes of RFID tags and has become the standard in supply chain applications. EPCglobal is an affiliate of the United States' Uniform Code Council (UCC) and Europe's EAN International (EAN). Both of these organizations maintain the EAN.UCC System, which for years has managed worldwide barcode numbering assignments and barcode symbology standards.
Unfortunately, there is still not a single agreed-upon standard for RFID tags that are used in supply chains, although it is likely that one will emerge soon. For now, different retailers have decided to go with different "classes" as defined in EPCglobal specs:
Version 1.0 (Generation 1, or Gen 1)
- Class 0 tags—These tags are read-only (programmed only once), have 64- or 96-bit memory capacities, and operate in the UHF frequency band between 868 and 930 MHz.
- Class 0+ tags—These tags are identical to Class 0 tags but are rewriteable.
- Class 1 tags—These one-time programmable (OTP) tags can be updated once after being encoded with an EPC number; they have a 96-bit memory capacity and operate between 868 and 930 MHz.
Version 2.0 (Generation 2, or Gen 2)
Generation 2 (Gen 2) tags were recently developed to overcome radio frequency interference (i.e., lighting) and security concerns surrounding Gen 1 tags. In fact, Wal-Mart and the DoD now require Gen 2 tags when their suppliers ship with RFID tags. It appears that most other larger retailers that intend to require RFID will follow suit. There is currently a single class for Gen 2 tags, which has a memory capacity from 96 to 256 bits. The operating frequency band is 860 to 960 MHz, which is consistent with ISO 18000-6 standards, allowing this standard to better integrate and interoperate with other global standards. It also has promise.
It's the Future
Although slower than what was originally promised by RFID technology manufactures and pioneering retailers, RFID is surely and steadily moving toward becoming the standard in product identification in the supply chain. As costs drop further, technologies are perfected, and standards are finally settled, this powerful technology will almost certainly become as ubiquitous as the barcode.
Bill Rice is senior products editor at MC Press. He can be reached at






















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online