*PUBLIC authority is the default access for an object. OS/400 is a bit unique in that everyone has some authority to every object on the system. If you don't get authority from anywhere else (e.g., *ALLOBJ special authority, private authority, authority from an authorization list, etc.), then you get the authority defined for *PUBLIC. Many other operating systems don't have the concept of a "default" access.
So how and when is this default access set? *PUBLIC authority is set when an object is created. Once the object is created, you can change the authority using the OS/400 commands Grant Object Authority (GRTOBJAUT) or Edit Object Authority (EDTOBJAUT) or the OS/400 IFS commands Work with Authority (WRKAUT) or Change Authority (CHGAUT).
It's the initial setting of this authority that I'd like to discuss, however. You may have noticed that when you create most OS/400 objects, the Authority (or AUT) parameter defaults to a value of *LIBCRTAUT. What on earth does that mean, you ask? Let's look at Figure 1 for an explanation.
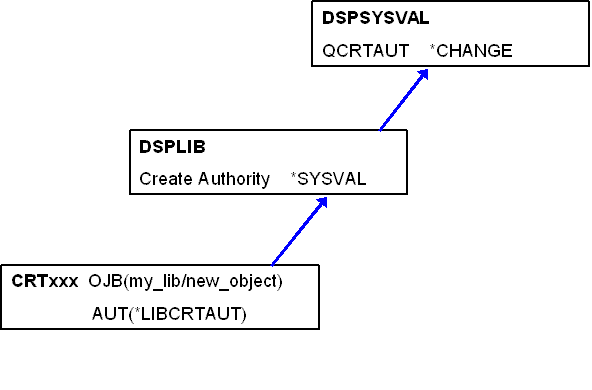
Figure 1: Here's how *PUBLIC authority is derived.
The value *LIBCRTAUT says to look at the Create Authority value for the library into which the object is being created. If you display the library using the Display Library Description (DSPLIBD) command, you will see that the value for the Create Authority parameter is *SYSVAL. What does this refer to? It refers to the value of the QCRTAUT (Create Default Public Authority) system value. The default for this system value is *CHANGE. That's why most objects end up with *PUBLIC authority *CHANGE. Obviously, when the object is created, the AUT parameter can be changed to another value such as *USE, *EXCLUDE, or the name of an authorization list. But most people just let it default, resulting in the object having *PUBLIC authority *CHANGE.
Please resist the temptation to start up an emulation session and quickly change your system's QCRTAUT system value to a more restrictive setting (such as *USE or *EXCLUDE.) While that may be what you end up doing after reading this column, there are some things you will want to consider before changing QCRTAUT to either *USE or *EXCLUDE.
First, there are some objects that require a user to have *CHANGE authority to use them--I'm speaking primarily of *DEVDs and *MSGQs. You might think about changing the command default for the Authority parameter of the Create Device Description (CRTDEVD) command to *CHANGE, but that won't do a lot of good when the system goes to auto-create a device and its corresponding message queue. Under the covers, OS/400 uses a different interface--not the CRTDEVD command to create devices. Therefore, unless you take some action, no one will be able to use the device descriptions or the message queues OS/400 automatically creates for you. You have two options. One is to manually update the authority to the device descriptions and their message queues, either giving everyone *PUBLIC authority or giving individuals *CHANGE authority to the device description and its message queue. The other is to change the Create Authority of QSYS to be *CHANGE.
If you change the Create Authority of QSYS, you will then want to change the command default for the Create Library (CRTLIB) command to be either *USE or *EXCLUDE (your preference). You may not realize it, but all libraries are created into the system library QSYS. Therefore, the *PUBLIC authority of all libraries comes from the Create Authority of the QSYS library. Changing the default for the Authority parameter on the CRTLIB command will ensure that all libraries are created with the appropriate *PUBLIC authority.
Another consideration is how changing this value will affect your applications. If your application authorization model depends on users having access through *PUBLIC authority and your application dynamically creates objects (e.g., files or data areas) application users need to read or update, your application might fail with a "Not authorized" message. Hang on--there's an answer to this problem. Remember the Create authority parameter on libraries? It defaults to *SYSVAL, but you can change that parameter to a value such as *USE or *EXCLUDE or even an authorization list name. So you can change the QCRTAUT system value to one value, such as *EXCLUDE, and change the Create authority parameter of your application's query library to *USE. Then, when an object is created into this library, the value specified in the Create authority value will be used for the object's *PUBLIC authority. Therefore, all new queries will be created with *PUBLIC authority *USE. Note that changing the Create authority parameter does not affect the *PUBLIC authority of existing objects in the library.
With more applications creating objects into the IFS, you might wonder how *PUBLIC authority defaults for those objects. This will be a topic of a future "Security Patrol" column.
A Completely Different Subject
Now, if you'll allow, I'd like to redirect your thoughts to something that has absolutely nothing to do with security. Rather, it has to do with what is going to occur during the next few weeks--the holiday season. Unfortunately, we often get caught up in the hustle and bustle of the season and don't take time to enjoy it. So the rest of this column is dedicated to tips to help you enjoy the weeks between now and the end of 2002.
Tip #1
Set reasonable expectations for yourself and your family--in other words, be realistic and carefully plan your schedule. At some point, we must face the fact that we are not supermen and superwomen. You cannot physically attend every event that is scheduled for this time of year. For example, you might limit yourself to only one or two events per week between now and the end of the year. Once you decide on the limit, stick to it! This will make you stop and evaluate which events you really want to attend. Limiting your activities will preserve your energy and your sanity!
Tip #2
Have some self-control. Have you ever noticed that diet food and exercise machines go on sale the first week of January? Ever gotten a sick feeling when you receive your credit card bill in January? Determine that you are going to have self-control this year. You can probably recite all the popular tips for not overeating--don't go to a party starved, drink lots of water, and so on. And I'm sure your intent is not to overspend. However, until you decide in your heart to exercise self-control, you are doomed to failure again this year. My advice is to tell someone that you're trying to control your urges--your spouse, a family member, or perhaps a close friend. It doesn't matter who you choose, as long as it's someone you trust who is willing to help keep you on track.
Tip #3
Be thankful! Did you ever notice that most merchants jump directly from Halloween into Christmas? Those of us in the United States are about to celebrate Thanksgiving. We all have many things to be thankful for. Forget for a moment the turmoil and troubles in the world today and reflect on the things you have to be thankful for. Then, carry that thankful heart all the way through the holiday season.
Tip #4
Perform your activities with joy. People will be celebrating the upcoming season in many different ways. Whatever our reasons to celebrate are, we all have reasons to experience and share joy. But we often forget these reasons and abandon the spirit of joy as we elbow our way to the front of the line at the shopping mall in our quest to find the absolute best deal on that holiday gift.
Tip #5
Be generous--share your joy. Keep your thankful heart past Thanksgiving and share it throughout the holiday season. Sharing your joy will plant a smile on your face, and your attitude will be contagious to all those you come in contact with. Remember, it is always better to give than to receive. What better gifts to give than a thankful heart and a spirit filled with joy.
Thank you for letting me divert briefly from my technical writing. I wish you great joy this holiday season.
Carol Woodbury is co-author of the book Implementing AS/400 Security as well as co-founder of SkyView Partners, a firm specializing in security consulting and services. Carol has 13 years in the security industry, 10 of those working for IBM's Enterprise Server Group as the AS/400 Security Architect and Chief Engineering Manager of Security Technology. Carol recently authored iSeries security training videos that are now available for purchase at www.expertanytime.com. Carol can be reached at


























 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online