Save the Best for Last Q: I have a nonindexed file that is read sequentially. Is it possible to get to the top of this file again after I hit the last record on a read?
Ñ Mamadou Toure
A: If you are using RPG IV, you can use the RPG IV keyword *START to get to the top of any file:
C *START SETLL FILE
In RPG III and RPG IV, to reposition the file to the first record for a nonindexed file, try this:
C 1 SETLL FILE
— Barbara Morris
RPG Compiler Development
IBM Toronto
Sorting It Out
Throughout OS/400, the capability exists to sort either in the “normal” sequence or by using a special sort table. The keyword you’ll find on the various commands that let you specify sorting is named SRTSEQ, and the default setting is *HEX, which sorts in sequence based on the hexadecimal values of characters in the field. You can also enter your own table name to perform the equivalent of ALTSEQ sorting.
There is, however, a special value, *LANGIDSHR, that provides some interesting features of its own. *LANGIDSHR sorts by the shared weight table that corresponds to the LANGID specified. What does the shared weight table do? Well, it basically sorts in a more user-friendly manner. Among other things, the shared weight table sorts fields in true alphabetical order regardless of case. Figure 1 shows how a few things would be sorted using *HEX. Because the hexadecimal representation of lowercase is lower than
uppercase, letters lower than numbers and blanks lower than punctuation, Figure 1 shows the normal list.
On the other hand, *LANGIDSHR sorts data as in Figure 2 because uppercase and lowercase letters have the same weight (hence, the weight is “shared”) as do blanks and punctuation, allowing a sort by actual text without regard to case. This method is useful when sorting things such as field de scri ptio ns. You will als o no tice tha t nu mbers are sorted before letters. This may be to conform with ASCII, in which digits have lower hexadecimal representations than characters. Be careful with this; it means the high-low range of “printable” alphanumeric characters is blank to Z rather than blank to 9, as with normal EBCDIC.
For other languages, *LANGIDSHR may act slightly differently. For instance, it may group accented letters with their unaccented equivalents. In addition, equivalently weighted values, such as uppercase and lowercase versions of the same word, are sorted in arrival sequence, so you may see the data sorted as it is in Figure 3. In Figure 1, “30 DAYS,” “30 days,” and “30-days” could appear in any order, depending on their arrival sequence. If your sorting must be case-sensitive, don’t use the *LANGIDSHR value!
To use the *LA NGID SHR opti on i n interactive SQL, press F13 to go to the SESSI ON a ttri bute s pa nel and chan ge t he S ort sequ ence par amet er t o *L ANGI DSHR . Fo r OP NQRY F, y ou c an s peci fy t he S RTSE Q (* LANG IDSH R) k eywo rd. This pa rame ter is a vail able on CRTL F, C RTPF , an d ot her file cre atio n co mman ds t o sp ecif y th e ha ndli ng o f ke y fi elds and to sele ct o r om it c rite ria and fiel d ed itin g. I t is al so a vail able wit h Cr eate RPG Pro gram (CR TRPG PGM) and oth er p rogr am co mpil atio n co mman ds t o sp ecif y in tern al t able , co mpar e, a nd s ort sequ enci ng. Ther e ar e ad diti onal con side rati ons; rev iew the help tex t fo r th e SR TSEQ key word of the sp ecif ic c omma nd y ou w ish to u se. *LAN GIDS HR c an a lso be d efin ed o r ch ange d at th e sy stem , us er p rofi le, and job leve ls. The syst em v alue is QSRT SEQ; for use r pr ofil es a nd j obs, the key word is SRTS EQ.
— Joe Pluta
AbACUS ABsolutely ABEND 30 cents 30 days 30 zebras 30 DAYS 30 MINUTES 30-days
Figure 1: You can sort data using the *HEX sequence.
30 cents 30 DAYS 30 days 30-days 30 MINUTES 30 zebras AbACUS ABEND About ABsolutely
Figure 2: *LANGIDSHR can also be used to sort data.
case cAse CASE case CASE casE
Figure 3: Equally weighted values are sorted in arrival sequence.
Empower Your Users
As with most AS/400 shops, my company needed to direct certain printed output to specific printers. After trying several methods to accomplish this, we decided on the following technique: We created a database that contains user ID/document/printer combinations. This method required the least amount of effort on our part while remaining accurate and effective.
When users initiate print jobs, we present them with a screen that displays the possible printers to which they can send their documents and suggests the “best” printer for the specific document. For example, if certain users should be printing only on printers defined w it h 8” x 1 5” c on ti nu ou s fe ed f or ms , we a cc om mo da te t he m by p re se nt in g a li st o f printers as defined in our user ID/document/printer database. Once they select a printer, we use the values defined in our database for that printer, apply them to the Override Printer File (OVRPRTF) command, and voilà! The document is routed to the correct printer!
When you initialize a program, this same method can be used so screen prints are routed to the correct printer and output queue. In such a case, apply the values from your user ID/program combination database to the Change Job (CHGJOB) command.
— Matti Kujala
Ahlstrom Kauttua Ltd.
Changing the Limit on the Number of Transfer Sessions
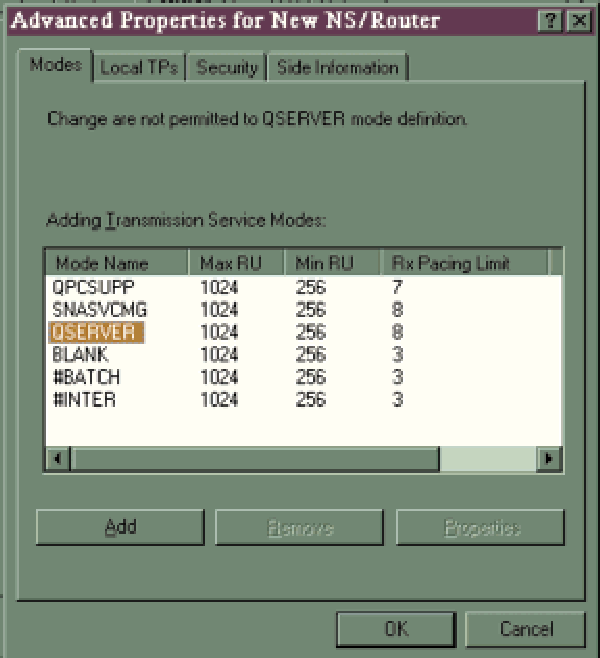
I am currently involved in a project using Visual FoxPro (VFP) to both send and retrieve data between the PC and the AS/400, and I ran into a problem in which VFP would “choke” when trying to open more than two remote files on the AS/400. After a lot of searching, I found a parameter under the Common tab in the NetSoft (NS) Router Administration panel. When I clicked on the Advanced Properties button of the Common tab, I found an entry for subsystem QSERVER and a category called Session Limit (see Figure 4). The number shown was 2, which was the same number of successful connections I could make. I wanted to change it to a much higher number, but the window stated that this parameter could not be changed. Now what?
I decided to look in the Windows NT Registry to see what I could find there. Using the RegEdit command (which you can reach by clicking on Start/Run, typing REGEDIT, and clicking OK), I opened the Registry and searched for the string QSERVER. Surprise! I found it under the key shown in Figure 5. I displayed the value of this key; lo and behold! It had a binary value of 2! I changed this to a binary value of 8 and was able to run my program successfully.
— Bill Robins
Figure 4: You can see the number of remote files you can create from the NS Administrator.
 |
HKEY_CURRENT_USERSoftwareNetSoftNS/Elite
CurrentVersionGlobalData5250
TransmissionServiceModeProfilesQSERVER
Figure 5: By changing this Windows Registry key, you can set the maximum number of remote files you can create through Client Access/400.
Quick! Help!
The Preventative Service Planning document for OS/400 V4R1 has a lot of great information. However, the part that catches my eye is the news that IBM Electronic Customer Support (ECS) has made a giant leap into the real world by adding several new phone lines and modems capable of running sessions at 19.2 Kbps. This means you can finally dump all those old and slow modems you thought you’d be stuck with forever.
If you have a modem capable of running at this speed (for example, the model
7852), you can improve the performance of your next PTF download. Take advantage of these new phone lines when contacting ECS by changing the number you dial to one of the following:
• 800-237-8804 (Eastern USA)
• 800-525-2834 (Western USA) For information on how to change the connection number for ECS on your system, refer to Chapter 7 of the AS/400 System Operation publication.
— David Boring
Systems Engineer, MCI Systemhouse
Who’s on the Job?
Looking for a way to know when a particular job starts, ends, or is placed on a job queue? You can get all this information by using the Job Notification Exit Point described in the “Work Management Exit Programs” chapter of the System API Reference. This exit program notifies you by subsystem whenever a job starts, ends, or is placed on a job queue. It’s also flexible enough for you to ask for only starts or only ends if that better meets your needs.
Ba sed on t he c rite ria you spec ify, whe n th e jo b st arts , en ds, or i s pl aced on a jo b qu eue, a n otif icat ion is s ent to a dat a qu eue. The inf orma tion sen t to thi s da ta qu eue incl udes bot h th e in tern al j ob i dent ifie r (a n in tern al h andl e us ed b y mo st A PIs to lo cate a s peci fic obje ct) and the name of the job itse lf. To k now prog ramm atic ally wh en a job sta rts, end s, o r is pla ced on a job que ue, crea te a mon itor ing prog ram that re ceiv es e ntri es f rom the data que ue. Once you hav e th e jo b in form atio n, y ou c an c all ot her APIs to do w hate ver you need to do i n re spon se t o th is a ctio n.
— Bruce Vining
IBM Rochester
Always Use a Key List When CHAINing
Factor 1 of an RPG CHAIN operation to an indexed file may contain either a variable name or a key list. For program-described files, factor 1 must contain a variable name. If the file is externally described and there are two or more key fields, factor 1 must contain a key list name. If the file is externally described and there is only one key field, factor 1 may contain either. It is always good practice to use a key list for externally described files, even when only one key field is used in the CHAIN.
Look at the code in Figure 6. The employee master file, EMPMAS, is keyed on a single field, EMPNO. If EMPMAS has 500 records, one of which is for employee 9295,
the CHAIN fails to find the record because it is looking for relative record number 9,295, not employee number 9295. The programmer has forgotten to include a K in the record address type field of the F-spec to indicate keyed access. This is an easy error to make and can result in debugging. If the programmer used a key list, as in Figure 7, the compiler would catch the error.
— Trent Holt
MTD Products, Inc.
Fempmas if e disk
C eval empno = 9295
C empno chain empmasr 99
C eval *inlr = *on
Figure 6: The compiler does not catch the programmer’s error.
Fempmas if e disk
C eval empno = 9295
C empkey chain empmasr 99
C eval *inlr = *on
C
C empkey klist
C kfld empno
Figure 7: Using a key list enables the compiler to catch the programmer’s error.
Emailing Messages and Files with the SNDDST Command
The Send Distribution (SNDDST) command enables you to send messages and files by email from a CL program or command line to non-AS/400 systems. You can send various types of information or objects with SNDDST. This tip explains three types of information and objects you can send: Long Message (*LMSG), File (*FILE), and Document (*DOC).
The *LMSG type allows you to send a message of up to 5000 characters. The only place I’ve seen documentation for *LMSG is on the cover letters for the PTFs mentioned at the end of this piece. *LMSG has only two formatting commands, :/N and :/P. :/N creates a new line, while :/P creates a new paragraph (which means a blank line and a new line). Here is an example of a SNDDST command using *LMSG and how the received email would look:
SNDDST TYPE(*LMSG) TOINTNET((
LONGMSG(‘This is a test message.:/NA new line.:/PA new paragraph.’)
SUBJECT(‘Tech Talk Long MessageDemo’)
This is a test message.
A new line.
A new paragraph.
You can also send physical files, logical files, or source files as email with SNDDST. This is an example of SNDDST used to send a file:
SNDDST TYPE(*FILE) TOINTNET((
DOCFILE(LIB/FILE)
DOCMBR(*FIRST) DOCTYPE(*FFT) SUBJECT(‘Tech Talk File Demo’)
This command places the contents of the file in the body of the email message. The trick is to specify a DOCTYPE of *FFT or 2, causing the file to be converted into ASCII text. There are limitations, however. SNDDST adds no carriage return and line-feeds characters to
the ends of records, so the beginning of the next record starts where the previous one stopped. In addition, source file records have their line numbers and date fields at the front, and packed decimal and binary fields are clobbered when SNDDST tries to convert their bytes into ASCII text.
Using the Copy to PC Document (CPYTOPCD) and Copy from PC Document (CPYFRMPCD) commands is a quick and dirty way to get the CR (Carriage Return) and LF (Line Feed) characters into a file (and get rid of the line numbers and date fields in source files). TRNFMT (Translation Format) (*TEXT) on CPYTOPCD adds the CR and LF, and TRNFMT (*NOTEXT) on CPYFRMPCD keeps them in the new file. The new file can have any record length, even 1 byte. SNDDST reads it as a stream of characters, and record length doesn’t matter. That’s what causes the formatting problem in the first place. When you send the new file with SNDDST, the text is formatted properly. Of course, if your file has a very long record length, it wraps around anyway because most email readers can’t properly display something that wide. Here are some examples:
* CPYTOPCD FROMFILE(LIB/OLDFILE) TOFLR(FOLDER)
FROMMBR(MEMBER) TODOC(PCDOX.TXT) REPLACE(*YES) TRNTBL(*DFT) TRNFMT(*TEXT)
* CPYFRMPCD FROMFLR(FOLDER) TOFILE(LIB/NEWFILE) FROMDOC(PCDOC.TXT) TOMBR(MEMBER)
MBROPT(*REPLACE)
TRNTBL(*DFT) TRNFMT(*NOTEXT)
SNDDST TYPE(*FILE) TOINTNET((
DOCFILE(LIB/NEWFILE) DOCMBR(*FIRST) DOCTYPE(*FFT) SUBJECT(‘Tech Talk File Demo’)
An email attachment is a better way to send a file, and this is where the *DOC information type comes in. First, copy the file to a PC document just as you did. Then, send the PC document. SNDDST looks something like the example below:
* SNDDST TYPE(*DOC) TOINTNET((
Document’) DOC(PCDOC.TXT) FLR(FOLDER) SUBJECT(‘Attached File’)
You still have to worry about packed decimal and binary fields being mangled, but everything else comes through OK.
Before you can use SNDDST as described above, you must prepare your system. You must first have SNADS, TCP/IP, and Simple Mail Transfer Protocol (SMTP) all configured and working properly. All of that is a tad beyond the scope of this piece, so go to the OS/400 TCP/IP Configuration and Reference manual if you haven’t done all of that stuff already. Next, if you are not using V4R3, you need to apply one set of the following PTFs:
• SF45257 and SF48224 for V4R2
• SF45226 and SF48223 for V4R1
• SF45415 for V3R7
• SF45328 for V3R2 On all OS versions, the Change Distribution Attributes (CHGDSTA) command must be executed to make SNDDST work with the Internet, and, for CHGDSTA to work, you must make an entry for a gateway to SMTP in your system directory. Details are on the help screens for the CHGDSTA command.
— Guy Murphy
FACTS Systems, University of Illinois
FTP Batch Transfer from AS/400 to PC
Looking for a way to get data from your AS/400 to your PC in batch mode? Well, if your PC is attached to your AS/400 via TCP/IP or even a shared network, you can do it. Look at the code in Figure 8. This is a batch program named MYFTP.BAT. MYFTP.BAT uses the FTP switch -s to indicate that the batch program—the PC file extension of *.BAT—uses another file (MYFTP.CMD) for FTP commands.
Now, look at the code in Figure 9. This file contains the commands to connect to my AS/400. The second and third lines are my user ID and password. The FTP command get is used to download the file from the AS/400 to the PC. In this case, it downloads a file named CFM05P from the library named SCHEDULE and places that file on my PC’s hard drive in a file named CFM05P.TXT. When the FTP program finishes downloading, it ends via the FTP command quit. Notice that all the commands are in lowercase. This distinction is important because FTP is an import from UNIX, and UNIX is case-sensitive.
Adding this batch program to an application’s macro or even to a scheduling system on your PC is now a simple matter. This method allows your users to download data without needing to run to you for help every time.
Ñ Shannon O’Donnell
Associate Technical Editor
Midrange Computing
— Brad Stone
Associate Technical Editor
Midrange Computing
FTP -s:C:windowsmyftp.cmd
Figure 8: Use this PC batch program to download data from your AS/400.
open 100.59.191.50
SHANNON
MYPASSWORD
get SCHEDULE/CFM05P C:CFM05P.TXT
quit
Figure 9: These FTP commands connect to and download AS/400 data.





















 More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment.
More than ever, there is a demand for IT to deliver innovation. Your IBM i has been an essential part of your business operations for years. However, your organization may struggle to maintain the current system and implement new projects. The thousands of customers we've worked with and surveyed state that expectations regarding the digital footprint and vision of the company are not aligned with the current IT environment. TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now.
TRY the one package that solves all your document design and printing challenges on all your platforms. Produce bar code labels, electronic forms, ad hoc reports, and RFID tags – without programming! MarkMagic is the only document design and print solution that combines report writing, WYSIWYG label and forms design, and conditional printing in one integrated product. Make sure your data survives when catastrophe hits. Request your trial now! Request Now. Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works.
Forms of ransomware has been around for over 30 years, and with more and more organizations suffering attacks each year, it continues to endure. What has made ransomware such a durable threat and what is the best way to combat it? In order to prevent ransomware, organizations must first understand how it works. Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include:
Disaster protection is vital to every business. Yet, it often consists of patched together procedures that are prone to error. From automatic backups to data encryption to media management, Robot automates the routine (yet often complex) tasks of iSeries backup and recovery, saving you time and money and making the process safer and more reliable. Automate your backups with the Robot Backup and Recovery Solution. Key features include: Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new.
Business users want new applications now. Market and regulatory pressures require faster application updates and delivery into production. Your IBM i developers may be approaching retirement, and you see no sure way to fill their positions with experienced developers. In addition, you may be caught between maintaining your existing applications and the uncertainty of moving to something new. IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
IT managers hoping to find new IBM i talent are discovering that the pool of experienced RPG programmers and operators or administrators with intimate knowledge of the operating system and the applications that run on it is small. This begs the question: How will you manage the platform that supports such a big part of your business? This guide offers strategies and software suggestions to help you plan IT staffing and resources and smooth the transition after your AS/400 talent retires. Read on to learn:
LATEST COMMENTS
MC Press Online